At this point in my career I don’t want to waste any more of my time working with Microsoft technologies. If a company is going to hire me, I will make sure that they don’t use Microsoft at all. Unless they contact me because they are looking for a way out.
This might sound like an elitist and presumptuous thing to say but there is actually a valid reason for that.
While all Microsoft technologies are infuriating due to their restrictive and close-sourced design, this is not the main focus of this article. Instead, it’s about privacy.
You see, most companies that rely on Microsoft technologies happen to use multifactor authentication. In other words, these companies require their employees to register their personal phone number and for them to be connected to Microsoft services in order to do their job. This is under the auspices of enhanced security and better privacy. In reality, this is the complete opposite because that’s forgetting that Microsoft has a horrible track record of avoiding data breaches. While the practice of 2FA theoretically benefits the company (although it really doesn’t because companies still get hacked every day of the year), it does not protect the employees from having their data stolen. As a matter of fact, it’s even worse because, when a data breach happens, hackers now also have access to employees’ phone numbers on top of all the information already available.
And do I want to be held accountable for Microsoft’s negligence? No. Therefore I prefer to abstain and not use anything that’s related to Microsoft.
Long story short: here is one fireproof tip I use to detect whether a company uses Microsoft technologies.
Please note I daily drive Gentoo Linux, so the article will focus on instructions for this particular distribution, but any other Linux distribution will do (Ubuntu, Fedora, Linux Mint, etc.). Just check your package manager for exact installation instructions.
We are going to need the “dig” command, which is part of the net-dns/bind package, so make sure it is installed before proceeding. Run this command as root:
1# emerge --ask net-dns/bindOnce the package is installed, just run the following command as a normal user:
1$ dig example.org MXThis command will pull up information that is specific to a company’s mail server (or MX, which is short for Mail eXchange). Just replace ’example.org’ with a domain name of your choice.
With microsoft.com, this is the result we get:

The value .mail.protection.outlook.com. indicates that Microsoft’s e-mail protection services are used, which sit on top of Microsoft Exchange Server, their proprietary mail transfer agent (MTA), and that Outlook is the mail client. If Microsoft Outlook is used, you can rest assured that the whole Microsoft 365/Office suite (which includes Excel, Word, etc.) is used as well because Microsoft doesn’t sell one without all the others - it’s a complete package. There you go, this concludes our article.
Or is it really the end?
Naaah. Sometimes it’s not really obvious that a company uses Microsoft and their products based on the MX record alone because the latter points to a different value, so we need to “dig” up (pun intended) a bit further. Luckily we can reuse the same command, but this time with a different type of DNS record, namely TXT.
TXT records store various information about a company’s domain, like you and I would keep personal notes inside our house that make it truly our own. I hope this analogy makes it easily understandable.
Let’s go ahead and use the example of alpro.com (they have the best vegan yogurts!).
Based on the MX record itself, we cannot determine that they use Microsoft - see below.
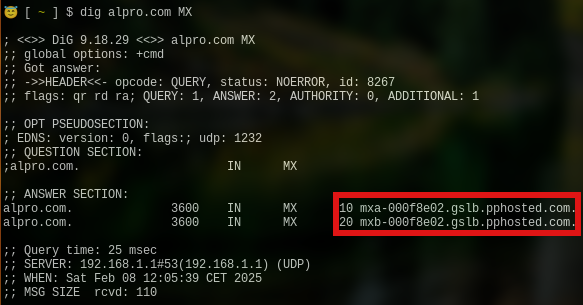
However, querying the TXT records gives it away immediately.
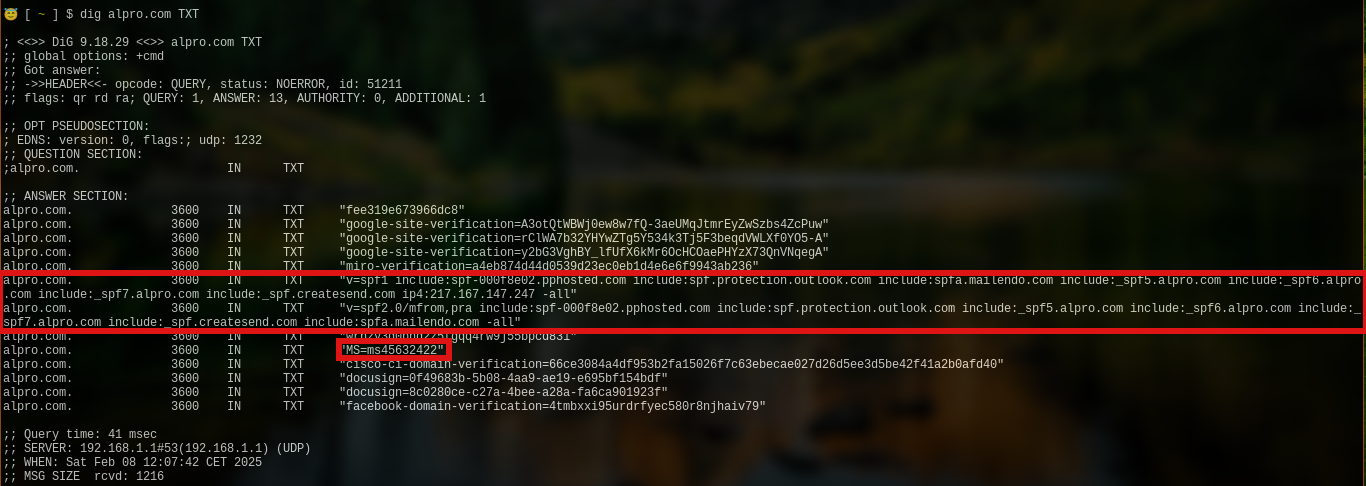
They even give you a little extra in the shape of "MS=ms45632422". This indicates the use of Microsoft 365 or Azure or other Microsoft-related products.
I love you, Alpro, but I think I would rather stay a customer. 😄
Try that yourself at home. And don’t be afraid of repercussions, this is public information.
#Microsoft #Privacy #Gentoo Linux #Multifactor authentication #English